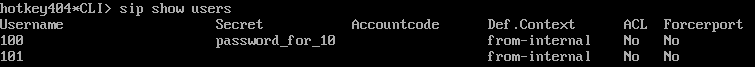Preventing anyone from seeing your passwords in the Asterisk CLI and only using it once (while creating the endpoint) seems like good practice for minimally more security. But let’s be honest. Using MD5 provides little or no security. Unless you’re using encrypted connections, the password is still sent in clear text.
Table of Contents
1) Why should you do so?
So far I found just one reason to use MD5. Then you can’t see the passwords in the CLI console.
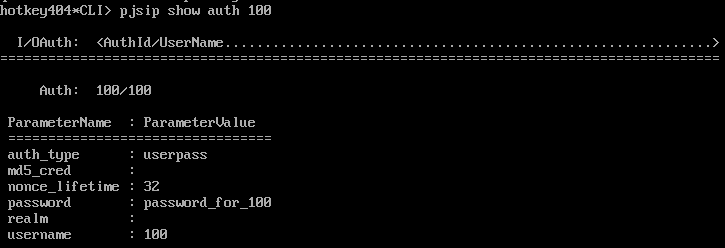
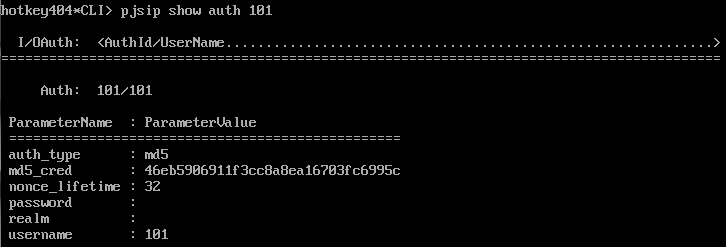
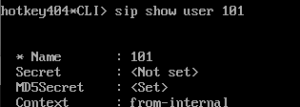
When you enter Asterisk CLI (asterisk -r) you can view all of the passwords.
| PJSIP | SIP |
|---|---|
Commands to view user info:pjsip show auths | Commands to view user info:sip show users |
Plain text password displayed in CLI
Plain text password hidden in CLI
| CLI displays secret (just first 15 characters) or empty when MD5 is used
Displaying info of specific user will only show which password (secret or md5secret) is set.
|
2) How-to
First, make sure Asterisk supports MD5 feature. To do this execute command below to check the availability of the mentioned feature. You can do this from your shell command.
asterisk -rx 'core show function MD5'
It should display MD5 function info.
If for some reason the function is not available you can load the appropriate module with the command: asterisk -rx 'module load func_md5.so' and add it in /etc/asterisk/modules.conf if necessary. If this does not help, it may be necessary to recompile Asterisk and mark the MD5 option in "make menuselect".
You can set custom realms for your endpoints. To check default realm type:
# for PJSIP
asterisk -rx "pjsip show settings" | grep "realm"
# for SIP
asterisk -rx "sip show settings" | grep "realm"
Since we have the required function, we can move on to password hashing. Before continuing, remember that a password actually consists of 3 parts: username, realm and password. The password is created as shown below:
md5secret = md5(username:realm:password)
To create the md5secret you may use linux command (providing all 3 variables):
echo -n "username:realm:secret" | md5sum
For example if you have your variables like
username=100
realm=asterisk
secret=Y0urS3cretP4ssword
hashing it will create md5secret like below.
echo -n "100:asterisk:Y0urS3cretP4ssword" | md5sum
3a4ebd8ef2dc6aad3af620447b5062fd
Adding -n for echo, so that the command doesn't add a newline to the end of the variable, thus generating an invalid md5 string.
2.1) PJSIP endpoint
In PJSIP endpoind’s password is stored in your endpoint’s auth context. First locate password of your endpoint. By default it will be located in /etc/asterisk/pjsip.conf file.
Then hash your password. In this example we will execute:
echo -n "100:asterisk:password_for_100" | md5sum
# result is 618b6c7ef2ed8faebd5ddc0170886c1f
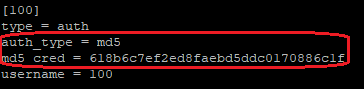
Then you need to make two changes:
- Change
auth_typefromuserpass(plaintext) tomd5 - Replace your line with
passwordwithmd5_credlike below:
To apply changes (unfortunately) you need to reload whole PJSIP module.
asterisk -rx "module reload res_pjsip.so"
You don’t have to make any changes in your endpoint (phone, gateway, etc..) because password remains the same. It’s just hidden in CLI console.
2.2) SIP endpoint
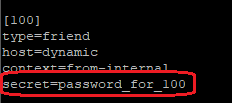
In SIP, endpoind’s password is stored in your endpoint’s context. First locate secret of your endpoint. By default it will be located in /etc/asterisk/sip.conf file.
Then hash you password. In this example we will execute:
echo -n "100:asterisk:password_for_100" | md5sum
# result is 618b6c7ef2ed8faebd5ddc0170886c1f
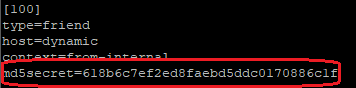
Then replace your line with secret with md5secret like below:
To apply changes reload your SIP config.
asterisk -rx "sip reload"
You don’t have to make any changes in your endpoint (phone, gateway, etc..) because password remains the same. It’s just hidden in CLI console.
3) Words of caution
The are a few thing that you need to know!
If there is an md5secret set in you SIP (not PJSIP) endpoint configuration, the secret for that user will be ignored!
It’s true: You cannot un-hash an MD5 hash and you can’t get back the original content from the hash. However with some work, you can craft two text strings that hash to the same hash. Also, you can find online tools that use a dictionary to retrieve the original un-hashed text string. This will provide our intruder with username, realm and secret separated by ‘:’ sign.
Still …. preventing every from seeing your passwords in Asterisk CLI and using it just once (during endpoint creation) seems like a good practice providing a little more security. Just remember to clear this information from your ~/.bash_history. Otherwise typing cat ~/.bash_history will display all your passwords!
And above all else …
DON’T USE UNSECURE PASSWORDS FROM THIS TUTORIAL!
Do you really know what is happening on your PBX? Try our proprietary VOIPERO software.
The system arleady has launched and now is completely FREE. Setup takes only a few minutes.
Read what our VOIPERO system can do in terms of live monitoring & reporting of VoIP systems based on Asterisk.