
Installing Asterisk 21 on AlmaLinux 9.3
Using Asterisk to build telecommunications systems can bring many benefits. Asterisk is available under an open source license, which means




Data leakage protection, work monitoring, security.

Data leakage protection, work monitoring, security.
80% of companies lose data due to employee errors or malicious activity. You can run your business without losing valuable intellectual property, copyrights or other data.
Discover and classify valuable data, audit all sensitive data activities anywhere to report and investigate where there’s a risk of leakage or theft.
Get your hybrid digital workspace under control, discover unwanted software and hardware, analyze behavior to detect and audit high-risk employees.
Protect sensitive business- or customer-related data, source codes, or blueprints from accidental or intentional leakage.
Choose a dynamic data loss prevention system and reach for a solution that allows for early detection and reduction of internal threats. The only on-premise and hybrid cloud data security solution designed with scalability in mind.
Our solution covers all areas of data security and internal threats. As specialists with almost twenty years of experience, we understand the internal risk to which data is exposed.
Never at the expense of performance. Our solution does not create unnecessary work for employees or the IT department, and its profitability index is unrivaled.
We ensure data protection on all workstations, various types of devices, the most important operating systems, environments working with the use of cloud services, devices in the company network and outside it.
At Safetica, we are experts in preventing human error. We make sure that you can return to work.





Security should never be at the expense of productivity. Our solution doesn’t create extra hassle for employees or the IT department, and its time-to-value is unbeatable.
Automation of security policies and integration with your IT stack help you protect your assets even in complex environments.
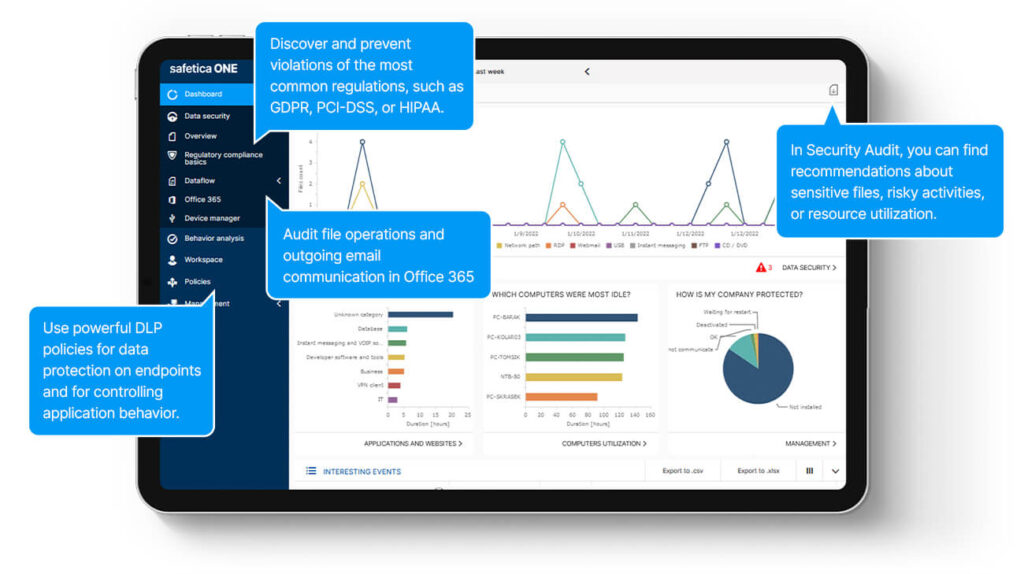
An all-in-one solution that integrates seamlessly into your existing security system can protect enterprise environments. That is why we secure data on all endpoints, all devices, all major operating systems (Windows, macOS), and the cloud, perimeters and internal zones.
Native integration with Microsoft 365 and Fortinet network appliances provides extended control over unknown devices and creates a robust endpoint-to-network security solution.
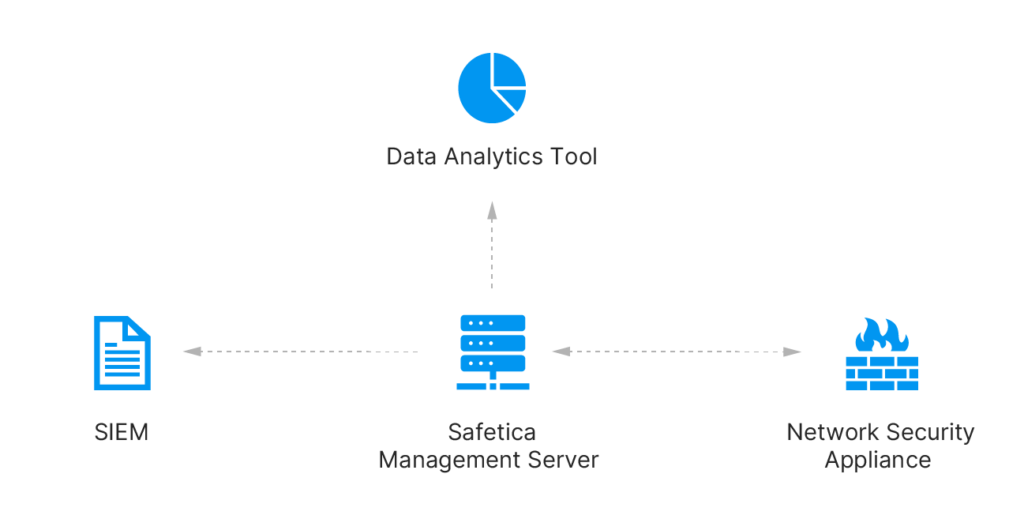
All audited incidents and logs can be automatically sent to SIEM solutions e.g., Splunk, IBM QRadar, LogRhythm, or ArcSight for further investigation. REST API provides collected data to tools like Power BI or Tableau for advanced analysis.
Understand sensitive data flow and classify your data. Get security & regulatory audit reports.
Integrate with your security stack and multi-domain environments.
Meets all safety requirements. Flexible and scalable for any IT environment.
Safetica ONE Discovery
Safetica ONE Enterprise
Test it for free before purchasing and choose the right solution for you: Safetica Enterprise or Discovery.
You can be sure that the system has been properly configured to meet the needs of your company.
By entrusting us with the administration of the system, you maintain full control and you can be sure that the security is correct and up-to-date.

Using Asterisk to build telecommunications systems can bring many benefits. Asterisk is available under an open source license, which means

Asterisk, as PBX software, is an extremely popular voice call management tool in companies around the world. Thanks to its

FreePBX is a powerful telephone PBX management platform that offers a range of functions, flexibility in customization, and rich integration

Who among us doesn’t like to use a free application, a free website or even a free cloud machine from
We Have Launched